Garmr is a tool to inspect the responses from websites for basic security requirements. It includes a set of core test cases implemented in corechecks that are derived from the Mozilla Secure Coding Guidelines which can be found here:
https://wiki.mozilla.org/WebAppSec/Secure_Coding_Guidelines
The purpose of this page is to establish a concise and consistent approach to secure application development of Mozilla web applications and web services. The information provided here will be focused towards web based applications; however, the concepts can be universally applied to applications to implement sound security controls and design.
This page will largely focus on secure guidelines and may provide example code at a later time.
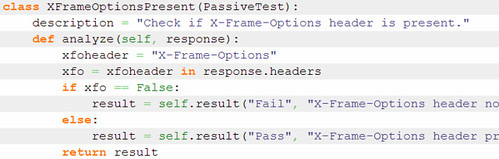
It’s a useful tool, combined with others to automate web application security tests to a decent, fairly comprehensive baseline. It was built to be part of a Continuous Integration process by the Mozilla WebQA team, but could easily be adopted by other teams and used in a similar way – it ouputs a JUnit style XML report that can be consumed by other tools such as Jenkins.
This is why it’s well suited to be used in a tool such as – Gauntlt – Security Testing Framework For Developers & Ops.
Usage
usage: Runs a set of tests against the set of provided URLs
[-h] [-u TARGETS] [-f TARGET_FILES] [-S] [-m MODULES] [-D] [-p] [-d]
[-r REPORT] [-o OUTPUT] [-c OPTS] [-e EXCLUSIONS] [--save DUMP_PATH]
optional arguments:
-h, --help show this help message and exit
-u TARGETS, --url TARGETS
Add a target to test
-f TARGET_FILES, --target-file TARGET_FILES
File with URLs to test
-S, --new-sessions Create new Session for each test
-m MODULES, --module MODULES
Load an extension module
-D, --disable-core Disable corechecks
-p, --force-passive Force passives to be run for each active test
-d, --dns Skip DNS resolution when registering a target
-r REPORT, --report REPORT
Load a reporter e.g. -r reporter.AntXmlReporter
-o OUTPUT, --output OUTPUT
Default output is garmr-results.xml
-c OPTS, --check OPTS
Set a parameter for a check (check:opt=value)
-e EXCLUSIONS, --exclude EXCLUSIONS
Prevent a check from being run/processed
--save DUMP_PATH Write out a configuration file based on parameters
(won't run scan)
A TARGET is an http or https scheme url to execute tests against.
e.g. garmr -u http://localhost
A MODULE is the name of a module; resolving this path needs to be improved
e.g. garmr -m djangochecks (Experimental)
An OPTS field contains the path and name of the option to set
e.g. garmr -m webchecks -c webchecks.RobotsTest:save_contents=True
A REPORT is the namespace qualified name of a reporter object or a valid alias (xml is the only current valid alias, and the default)
e.g. garmr -r xml
An EXCLUSION prevents a check from being executed
e.g. garmr -e WebTouch
Disable core checks will prevent all of the checks in corechecks from being loaded; this is useful to limit the scope of testing.
You can download the latest version here:
Or read more here.
The post Garmr – Automate Web Application Security Tests appeared first on Darknet - The Darkside.